Join the fight against malicious programs and cybercrime on our Computer Science Cyber Security MSc. Third-party forensic experts revealed that they had created and used a new form of ransomware called Phoenix CryptoLocker for this attack.

Malaysia Economic Crimes Conducted Through Cyber Attacks On Organizations 2017 Statista
We will give you the skills you need to become a Cyber Security and Digital Forensics professional intercepting collecting analysing and reporting the events in cyberspace and digital media.

. Management Development Institute of Singapore Singapore. A spate of ransomware targeting countries in the Global South has demonstrated an evolution in attackers tactics. He is regularly sought after for his ability to simplify complex.
It currently lists 42 equities from 37 companies and 2 corporate bonds. What are the Categories of Cyber Crime. Pay a minimum of 50 of your first-year tuition fees to Leeds Beckett University.
All types of securities can be listed. The A9Play app employs A9-Wallet with a built-in latest security system technology to secure your account against fraud hacking and other types of cybercrime. Therefore you will not encounter cyber-crime activity with your A9-Wallet and luckily there are no incidences of fraud that have been reported since we developed the A9Play gambling site.
They will develop a broad knowledge of the field of security and crime science and a familiarity with the latest academic research through studying with world-leading experts. Potential to build capital and surplus as well as fund insurance claims by paying and setting aside premium payments and underwriting investments to cover losses. They also have the opportunity to study crime prevention methods in depth and acquire knowledge of different types of crime such as cybercrime or organised crime.
Cyber crimes are categorized into three broad categories individual property and government. The Office of Tailored Access Operations TAO now Computer Network Operations and structured as S32 is a cyber-warfare intelligence-gathering unit of the National Security Agency NSA. He has also been recognised by Benchmark Litigation as a Future Star in the areas of Commercial and transactions 2019 2021 Construction Insolvency and Labour Employment 2019 2021.
It has been active since at least 1998 possibly 1997 but was not named or structured as TAO until the last days of 2000 according to General Michael Hayden. Hong Kong College of Technology Hong Kong. Rushmore Business School Mauritius.
Based on each category of cyber crime cybercriminals use different levels and types of threats. Differences stem from a lack of common vision on the parameters of cybercrime internet governance and digital sovereignty as well as for regulation of online content and access to data. Better approach to funding for future catastrophic losses such as cybercrime terrorism and product liability.
Gathering the latest threat intelligence from around the world Trend Micro Research continuously explores the threat landscape to bring you the trusted insights you need to withstand threats now and in. Human trafficking slavery and slavery-like practices such as servitude forced labour and forced marriage are complex crimes and a major violation of human rights. The hacker group Russian cybercrime syndicate Evil Corp was thought to be behind this attack.
Servitude Slavery Forced labour Debt Bondage Forced marriage or Organ harvesting Australia is primarily. Eddie was awarded Young Lawyer of the Year by the Asian Legal Business Malaysia Law Awards 2018. Asian Institute of Built Environment Hong Kong.
Enterprises need help to stay ahead of both simple ransomware attacks and advanced rapidly evolving cybercrime operations. The British College Nepal. There are different types of cyber crimes that use malicious code to modify data and gain unauthorized access.
For example with a first-year tuition fee of 14000 and scholarship of 1000 the minimum would be 6500 50 of 13000. At their core these concerns boil down to issues of state control in terms of cooperation and data sharing with other states and in relation to countries control over their. As a leading voice in the fight against cybercrime we work tirelessly to discover key insights that allow us to protect 500K companies worldwide from 100s of millions of threats daily.
The Ghana Stock Exchange GSE is the principal stock exchange of GhanaThe exchange was incorporated in July 1989 with trading commencing in 1990. Criteria for listing include capital adequacy profitability spread of shares years of existence and management efficiency. Historically ransomware has targeted a number of high-value sectors finance professional services the public sector in wealthy countries concentrating on the US and other G7 membersRecent attacks on countries such as Costa Rica South.
Media reports stated that CNA Insurance agreed to pay 40 million as ransom to get back access to its network. Almost 11500 cyber events were reported to Switzerlands National Cyber Security Centre in the second half of 2021 alone and they are growing more sophisticated said Roger Albrecht co-lead ISG Cybersecurity. Around the world men women and children are trafficked for a wide range of exploitative purposes such as.
Coverage for unique risks that may be unavailable in a traditional insurance arrangement. College of Allied Educators Singapore. Full list of international.
Gaborone University College Botswana.
Cybercrime Which Ones Are The Most Common Threats Today Red Points

What Is Cybercrime Different Types And Prevention

20 Important Types Of Cyber Crimes To Know In 2022

Types Of Cybercrime Panda Security Mediacenter

10 Types Of Cyber Crimes And Another 10 You Ve Never Heard Of

Cybercrime Definition Types And Reporting Clearias
What Is Cyberstalking And How To Prevent It

Zeus Malware Double Threat How To Defend Yourself Against Zeus P1networks More Info Https Storify Com P1ne Malware Cyber Security How To Defend Yourself
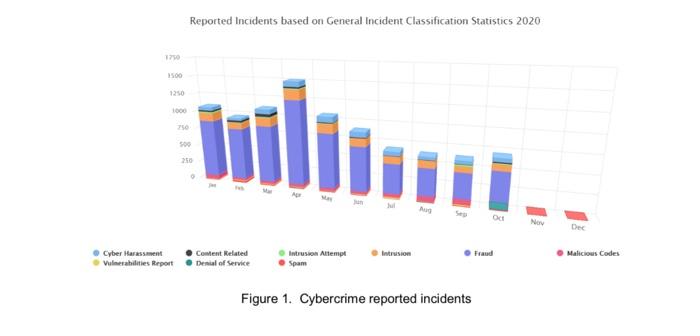
Solved The Cybercrime Report Registered In Malaysia Between Chegg Com
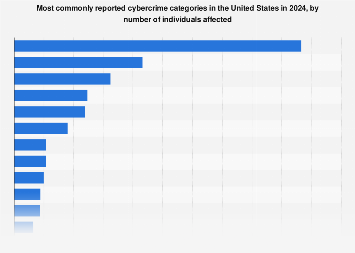
Most Frequently Reported Types Of Cyber Crime 2021 Statista

Most Frequently Reported Types Of Cyber Crime 2021 Statista

Types Of Cybercrime Panda Security Mediacenter

20 Important Types Of Cyber Crimes To Know In 2022

Cybercrime Emergence Types And Some Mitigating Steps

